The Unseen Threat: How Shadow IT Paves the Way for Ransomware Attacks
Understand the risks of shadow IT practices and their inadvertent facilitation of ransomware threats. Discover effective strategies to fortify your organizational defenses, mitigate vulnerabilities, and safeguard your data against the pervasive menace of shadow IT-induced ransomware infiltrations.
Unveiling the Differences Between Phishing and Spear Phishing: Know How to Protect Yourself
Discover the disparities between general phishing and targeted spear phishing, and fortify your defences against these prevalent cyber threats. Learn effective strategies to enhance your cyber resilience and safeguard your personal and organizational security effectively
Safeguarding Against Credential Dumping and Credential Reuse Attacks: A Comprehensive Guide
Learn about the critical significance of safeguarding credentials and the risks associated with credential reuse attacks. Explore effective strategies to fortify your digital security against credential dumping, and stay informed with expert insights and tips to protect your online presence effectively.
Safeguarding Your Data: The Perils of SQL Injection and Zero-Day Exploits
This blog delves into cybersecurity, spotlighting the critical risks of SQL injection and zero-day exploits. It highlights potential data breaches and system compromises. Offering defense strategies like security audits, intrusion detection, and staying updated, it advocates a proactive cybersecurity approach for safeguarding data and systems from these pervasive threats.
Protecting Your AWS Infrastructure: Understanding and Mitigating Cloud Cryptomining Threats
Cloud cryptomining exploits AWS resources to mine cryptocurrency, posing risks like system slowdowns and increased expenses. Protecting your AWS environment involves proactive measures: regular assessments, robust access controls, and vigilant monitoring. Staying updated on security measures and collaborating with experts ensures resilience against evolving threats, securing your cloud operations.
Decoding Cyber Security Threats: The Pitfall of Advanced Persistent Threats
Discover the ieats, mitigating risks with robust network monitoring and vigilant defense protocols. Stay ahead in the digital landscape with our comprehensive guide to cyber threat management.nsiious nature of Advanced Persistent Threats (APTs) and their reliance on Command and Control (C2) attacks. Learn how to fortify your cybersecurity strategy against these stealthy threats, mitigating risks with robust network monitoring and vigilant defense protocols. Stay ahead in the digital landscape with our comprehensive guide to cyber threat management.
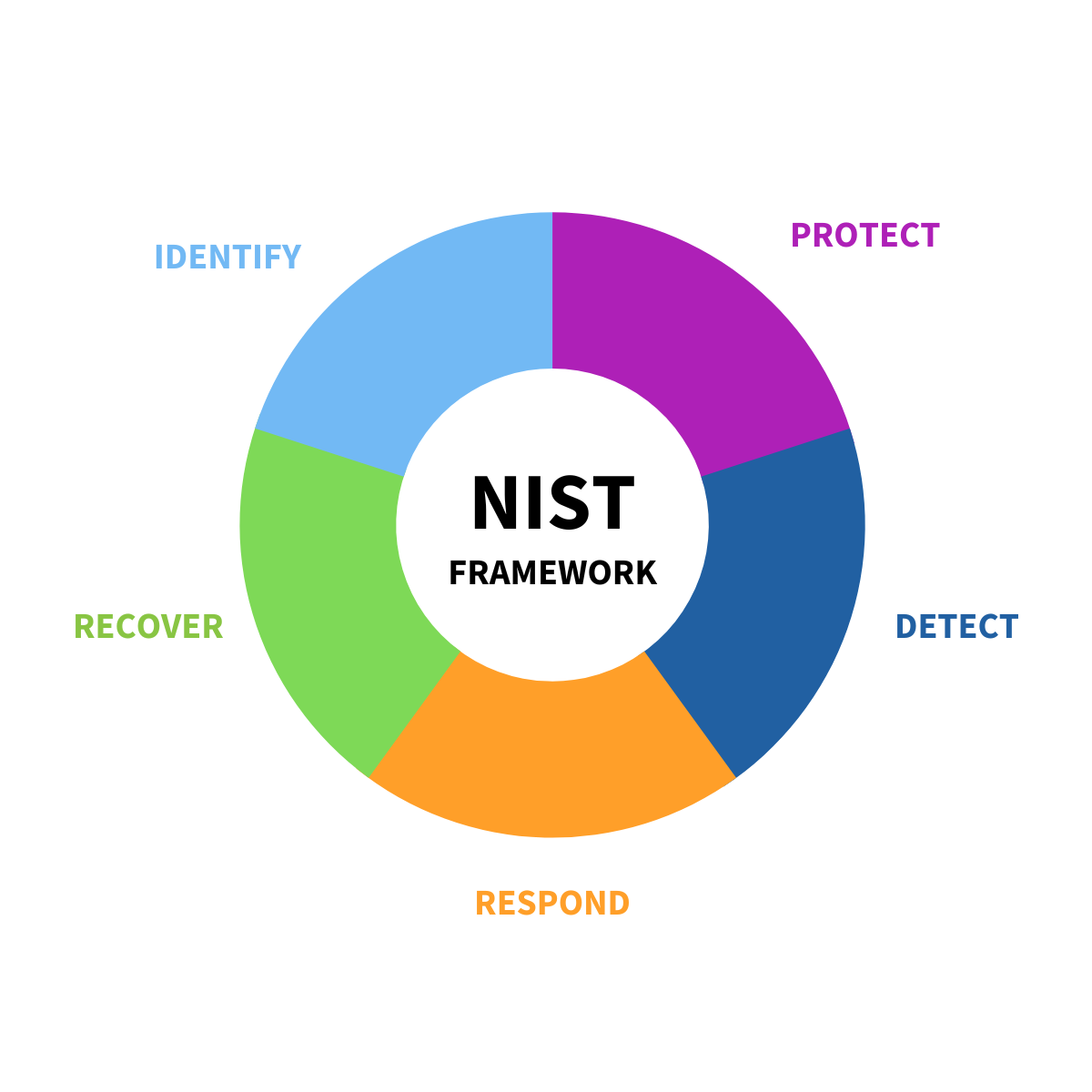
Strengthening cybersecurity governance with the NIST Framework
Explore the NIST Cybersecurity Framework and bolster your organization's cyber defenses. Learn how to leverage this structured approach to fortify governance, identify risks, protect assets, detect threats, respond efficiently, and recover post-incidents. Discover insights into proactive risk management in today's evolving threat landscape with itAgenturen's expert guidance.
Privacy best practices
Secure your Android app by following these simple tips. Only ask for the permissions you really need, and be clear about why. If someone denies a permission, make sure your app still works smoothly. Explain why you need location access and use it transparently. Keep sensitive data safe, use resettable IDs, and respect user preferences. Following these tips not only keeps your app secure but also makes users trust and enjoy it more.