Safeguarding Your Data: The Perils of SQL Injection and Zero-Day Exploits
In today's digital landscape, cybersecurity remains a crucial focal point for businesses, with the persistent threats of SQL injection and zero-day exploits looming large. Understanding the risks associated with these vulnerabilities is paramount in fortifying your data against malicious attacks and preserving the integrity of your systems.
Decoding SQL Injection Threats
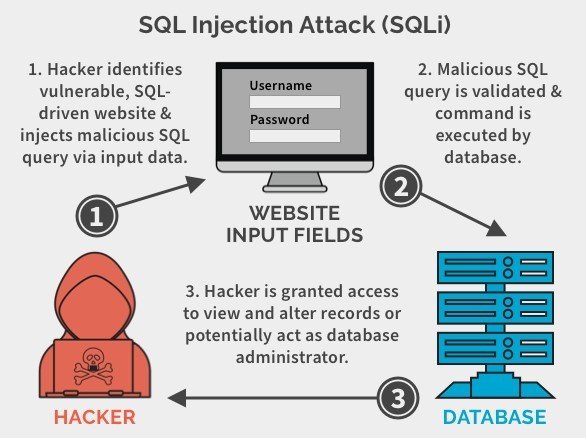
SQL injection is a widespread cyber threat that targets databases, exploiting vulnerabilities to manipulate the commands that interact with the database, thereby enabling unauthorized access. This insidious technique poses a severe risk, potentially leading to data breaches, data loss, and even complete system compromise. Recognizing the signs of SQL injection and implementing robust security measures is vital in mitigating this threat.
Unveiling the Dangers of Zero-Day Exploits
Zero-day exploits, on the other hand, refer to previously unknown vulnerabilities that hackers can exploit to gain unauthorized access. These vulnerabilities often surface with little to no warning, leaving businesses vulnerable to cyber-attacks. Zero-day exploits can result in data breaches, system malfunctions, and significant financial losses, emphasizing the urgency of proactive security measures and comprehensive vulnerability management strategies.
Protecting Your Systems: Best Practices
To fortify your systems against SQL injection and zero-day exploits, it is crucial to establish stringent security protocols. Conducting regular security audits, implementing strict access controls, and deploying robust intrusion detection systems can significantly reduce the risks posed by these threats. Moreover, staying informed about the latest security patches and updates is essential in preventing potential vulnerabilities from being exploited.
The Interconnected Threat Landscape
What makes the dangers of SQL injection and zero-day exploits even more critical is their interconnected nature. In some instances, cybercriminals can utilize SQL injection techniques to identify and exploit unknown vulnerabilities, creating a pathway for zero-day attacks. By manipulating input fields and injecting malicious code, attackers can gain access to sensitive data and potentially discover unpatched vulnerabilities, paving the way for zero-day exploits.
Understanding this relationship underscores the importance of adopting a holistic security approach that addresses all potential entry points. Integrating robust security measures, conducting regular vulnerability assessments, and prioritizing the timely application of security patches can effectively mitigate the risks posed by both SQL injection and zero-day exploits, safeguarding your data and systems from malicious cyber threats.
Staying Ahead in the Cybersecurity Landscape
As cyber threats continue to evolve, so must our defense strategies. By maintaining a proactive approach to cybersecurity, businesses can safeguard their data and systems from the pervasive risks posed by SQL injection and zero-day exploits. Investing in comprehensive cybersecurity solutions and fostering a culture of vigilance can go a long way in ensuring the resilience and security of your digital infrastructure