Spring Tool Suite(STS):Role Based User Aunthentication using STS
What is STS?
Spring Tool Suite (STS) is an integrated development environment (IDE) specifically designed for building applications using the Spring Framework. It's based on Eclipse and provides a comprehensive set of tools for developing, testing, and deploying Spring-based applications efficiently.
STS simplifies the development process by offering features like:
Spring-specific tools: It includes various wizards, templates, and editors tailored for Spring applications, enabling developers to easily create and manage Spring projects.
Code assistance and navigation: STS provides intelligent code completion, quick navigation, and refactoring tools specific to Spring components, making it easier to work with complex Spring configurations.
Integrated server support: It seamlessly integrates with servers like Apache Tomcat, enabling developers to deploy and test their applications directly from the IDE.
Advanced debugging: STS offers debugging capabilities that allow developers to troubleshoot applications effectively by providing step-by-step debugging, breakpoints, and inspection of variables.
Support for various Spring technologies: It supports different Spring modules such as Spring Boot, Spring Data, Spring Security, etc., making it versatile for a wide range of Spring-based projects.
Extensive plugin ecosystem: Developers can extend STS's functionality by adding plugins from a vast repository, customizing the IDE to fit their specific project requirements.
Using STS streamlines the development of Spring applications, offering a user-friendly environment that caters to the unique needs of Spring developers.
Role Base User Aunthentication using STS:
Role-based user authentication in Spring Tool Suite involves leveraging Spring Security, a powerful framework that manages authentication, authorization, and access control in Spring-based applications.
Theoretical Overview:
Authentication:
Authentication is the process of verifying the identity of users. In Spring Security, this can be achieved through various mechanisms such as in-memory authentication, JDBC authentication, LDAP, OAuth, etc. Once authenticated, users receive a security context that includes their identity and granted authorities (roles).
Authorization:
Authorization determines what authenticated users are allowed to do within an application. Spring Security uses roles or authorities to control access to specific parts of the application. Roles represent specific permissions or responsibilities granted to users.
Role-Based Access Control (RBAC):
RBAC is a common approach in Spring Security where access to resources or functionalities is restricted based on the roles assigned to users. Each role defines a set of permissions, and users are granted these roles to access corresponding functionalities.
Implementation Steps:
Configuration: Define security configurations to specify access rules and authentication mechanisms. This involves setting up a WebSecurityConfigurerAdapter class to customize security settings and access rules.
Role Assignment: Users are associated with specific roles. These roles are typically defined in the system and are linked to different levels of access or permissions.
Access Control: Configure URL patterns and authorize access to specific endpoints or functionalities based on roles using antMatchers() in the security configuration.
Testing and Validation: Verify the implementation by testing with different user roles to ensure that access control is working as intended.
Benefits:
Granular Access Control: Allows fine-grained control over which users can access certain functionalities based on their roles.
Security: Helps protect sensitive parts of the application from unauthorized access, reducing the risk of data breaches or misuse.
Challenges:
Managing roles and their associated permissions effectively can become complex in larger applications.
Ensuring proper enforcement of access control across the entire application requires meticulous configuration and testing.
In essence, Spring Tool Suite, combined with Spring Security, provides a robust framework for implementing role-based user authentication. It allows developers to control access to different parts of an application based on the roles assigned to users, ensuring a secure and controlled environment for users interacting with the application.
Implementing Role-Based User Authentication in Spring Tool Suite using Spring Security: Step-by-Step Guide
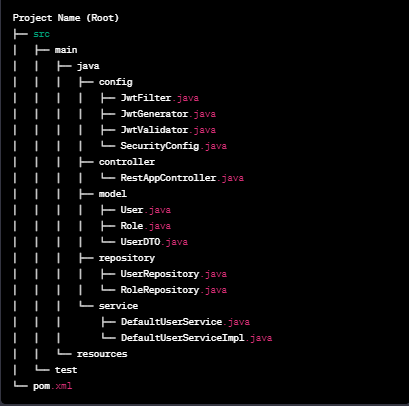
1)Project Structure Breakdown
1)config: Contains security-related classes (e.g., JWT filter, security configurations).
2)controller: Handles HTTP requests through RestAppController.
3)model: Defines entities like User, Role, and UserDTO.
4)repository: Provides data access via UserRepository and RoleRepository.
5)service: Implements business logic in DefaultUserService and DefaultUserServiceImpl.
Key Folders:
src/main/resources: Holds application configuration files.
src/test: Potentially contains test suites for validating application functionality.
This structured layout compartmentalizes functionalities for clarity and maintainability, adhering to best practices in Spring application development.
Now let’s start with the development of the project
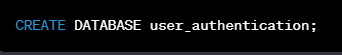
Lets start with the Database setup, we wil be using PostgreSQL to implements this project.
Whatever it is, the way you tell your story online can make all the difference.
Start by creating a data base or using an existing database, as mentioned above .
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
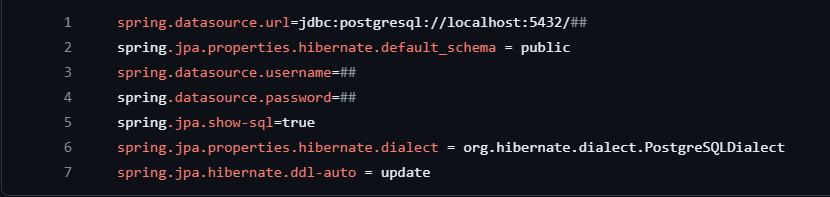
1)spring.datasource.url=jdbc:postgresql://localhost:5432/##: This line specifies the URL for the PostgreSQL database. The URL generally follows the format jdbc:postgresql://<host>:<port>/<database_name>. Ensure to replace your_database_name with the name of your specific PostgreSQL database.
2)default_schema: Specifies the default schema where your tables will be created.
3)show-sql: If set to true, enables the logging of SQL statements to the console.
4)hibernate.dialect: Defines the dialect for Hibernate to interact with PostgreSQL.
5)hibernate.ddl-auto: Defines how Hibernate manages the database schema. update mode updates the schema if changes are detected in the entity models.
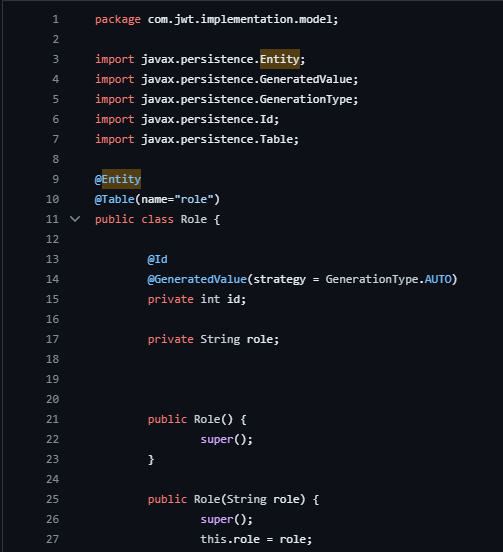
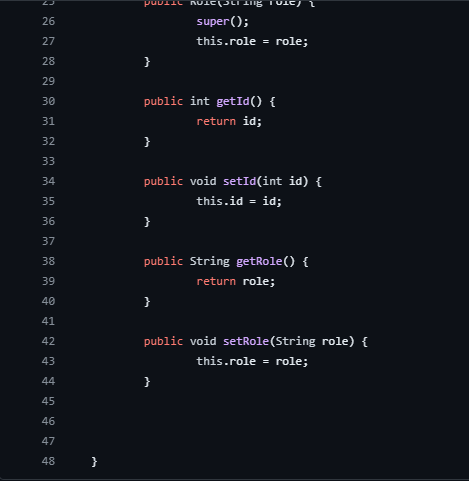
Role.java
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: The class is part of the com.jwt.implementation.model package.
Annotations (@Entity and @Table): Specifies that this class is an entity mapped to a database table named "role".
Class Definition (public class Role): Defines a Java class named Role.
Fields:
private int id: An auto-generated unique identifier for the role.
private String role: Represents the role name.
Constructors:
public Role(): Default constructor.
public Role(String role): Constructor allowing initialization of the role attribute.
Getter and Setter Methods:
getId() and setId(int id): Accessor methods for the id attribute.
getRole() and setRole(String role): Accessor methods for the role attribute.
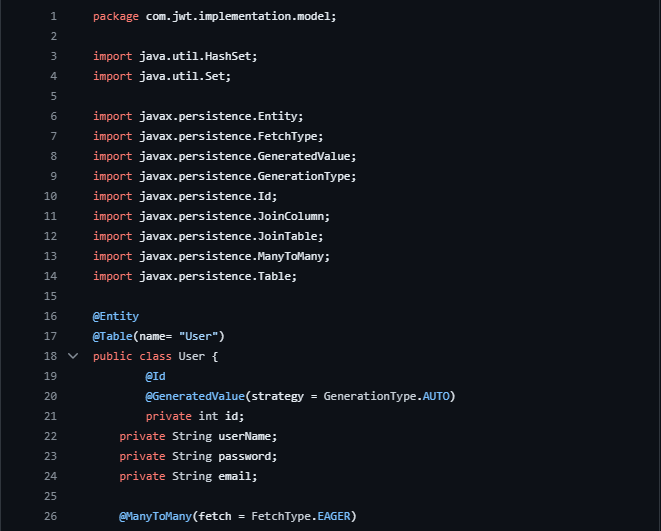
User.java(in the model package)
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: The class resides in the com.jwt.implementation.model package.
Annotations (@Entity and @Table): Denotes this class as an entity mapped to a database table named "User".
Class Definition (public class User): Represents a Java class named User.
Fields:
private int id: Auto-generated unique identifier for the user.
private String userName: Stores the username.
private String password: Holds the user's password.
private String email: Stores the user's email address.
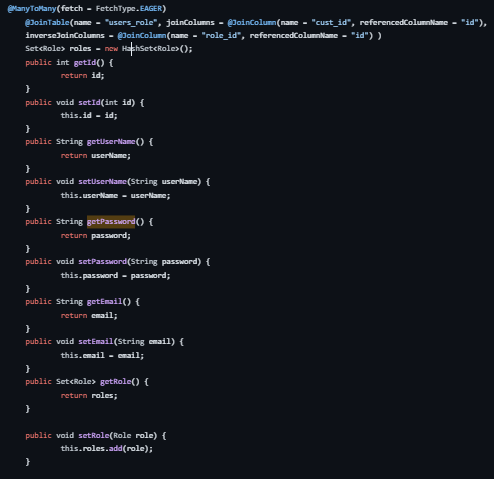
@ManyToMany Relationship:
Establishes a many-to-many relationship with the Role entity.
fetch = FetchType.EAGER: Specifies eager loading of roles.
@JoinTable: Configures the join table name and columns for the relationship between users and roles.
Roles Handling:
Set<Role> roles = new HashSet<Role>(): Initializes a set to store roles associated with the user.
setRole(Role role): Adds a role to the user's set of roles.
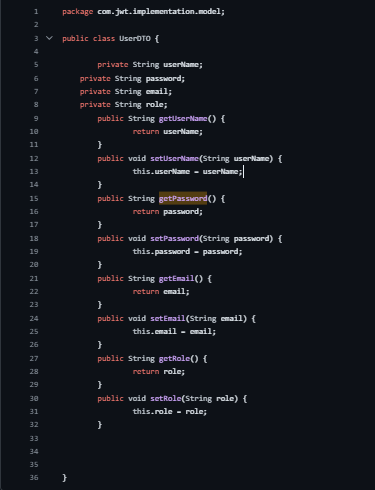
UserDTO Class in Spring: Data Transfer Object for User Information
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: This class resides in the com.jwt.implementation.model package.
Class Definition (public class UserDTO): Represents a Java class named UserDTO.
Fields:
private String userName: Holds the username.
private String password: Stores the password.
private String email: Contains the user's email address.
private String role: Represents the role associated with the user.
Getter and Setter Methods:
Accessor methods for 'userName', 'password', 'email', and 'role'.
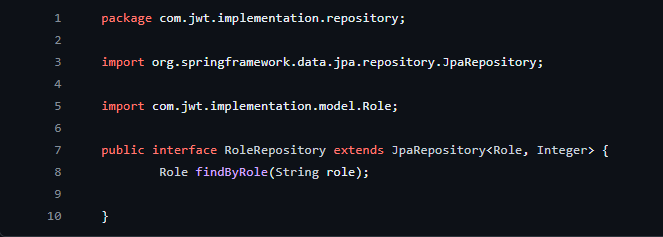
RoleRepository Interface in Spring: Handling Role Data Access with JpaRepository
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: The interface resides in the com.jwt.implementation.repository package.
Interface Definition (public interface RoleRepository): Defines an interface named RoleRepository.
Extends JpaRepository: Extends the JpaRepository interface, indicating that it's a repository interface for the Role entity. The JpaRepository provides methods for basic CRUD operations.
Method:
Role findByRole(String role): Declares a custom query method. It defines a method to find a role by its name.
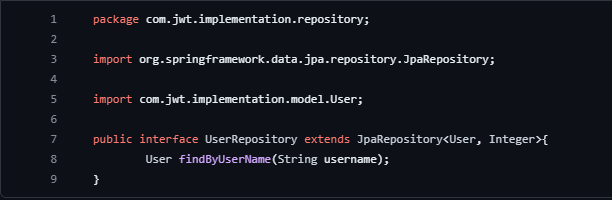
UserRepository Interface in Spring: Implementing User Data Access with JpaRepository
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: The interface is located in the com.jwt.implementation.repository package.
Interface Definition (public interface UserRepository): Defines an interface named UserRepository.
Extends JpaRepository: Extends the JpaRepository interface, indicating that it's a repository interface for the User entity. The JpaRepository provides methods for basic CRUD operations.
Method:
User findByUserName(String username): Declares a custom query method. It defines a method to find a user by their username.
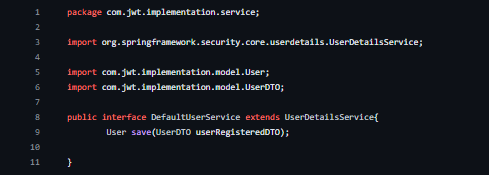
DefaultUserService Interface in Spring: Defining User Service Functionalities
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: The interface is located in the com.jwt.implementation.service package.
Interface Definition (public interface DefaultUserService): Defines an interface named DefaultUserService.
Extends UserDetailsService: Extends the UserDetailsService interface, indicating that it provides user-related service functionalities.
Method:
User save(UserDTO userRegisteredDTO): Declares a method to save user information based on the provided UserDTO.
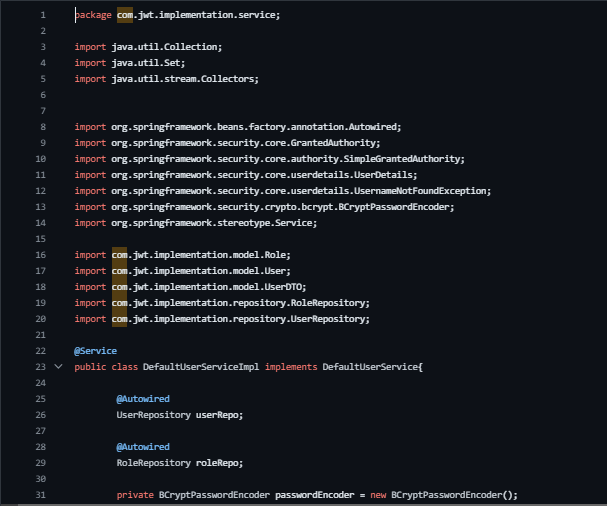
DefaultUserServiceImpl Class in Spring: Implementing UserDetailsService and User Registration
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: The class resides in the com.jwt.implementation.service package.
Class Definition (public class DefaultUserServiceImpl): Represents a class named DefaultUserServiceImpl.
Annotations (@Service, @Autowired):
@Service: Indicates that this class is a service component.
@Autowired: Injects instances of UserRepository and RoleRepository into the class.
Fields and Methods:
loadUserByUsername(String username): Implements the loadUserByUsername method from UserDetailsService, fetching user details for authentication.
mapRolesToAuthorities(Set<Role> roles): Maps roles to Spring Security GrantedAuthority.
save(UserDTO userRegisteredDTO): Saves user information from the provided UserDTO object.
BCryptPasswordEncoder: Handles password encoding using BCrypt for enhanced security.
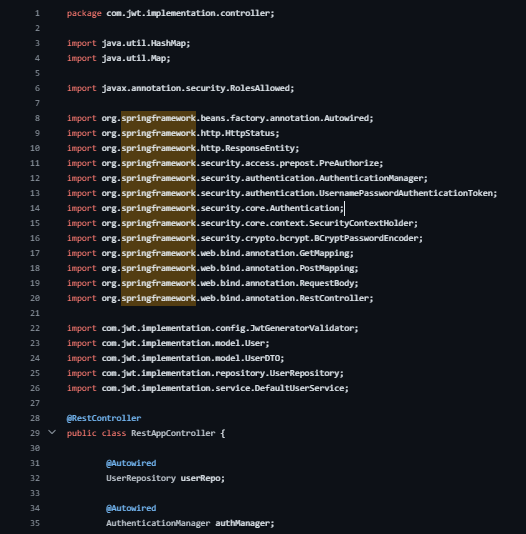
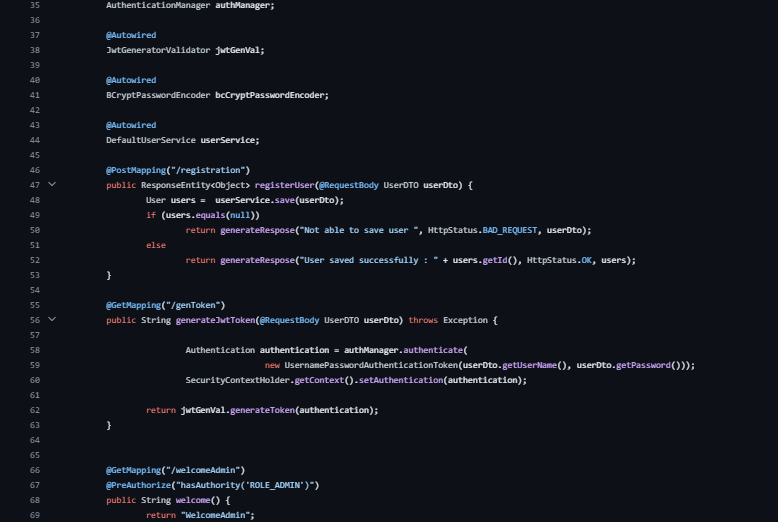
RestAppController in Spring: Handling User Registration, Authentication, and Role-Based Authorization
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: The class resides in the com.jwt.implementation.controller package.
Class Definition (public class RestAppController): Represents a RESTful API controller for handling various endpoints.
Annotations (@RestController, @Autowired, @PostMapping, @GetMapping, @PreAuthorize):
@RestController: Marks the class as a RESTful controller.
@Autowired: Injects instances of required classes (repositories, services, etc.).
@PostMapping, @GetMapping: Maps HTTP POST and GET requests to specific methods.
@PreAuthorize: Defines method-level security based on user roles.
Endpoints and Methods:
registerUser(UserDTO userDto): Registers a user with provided details.
generateJwtToken(UserDTO userDto): Generates a JWT token for authentication.
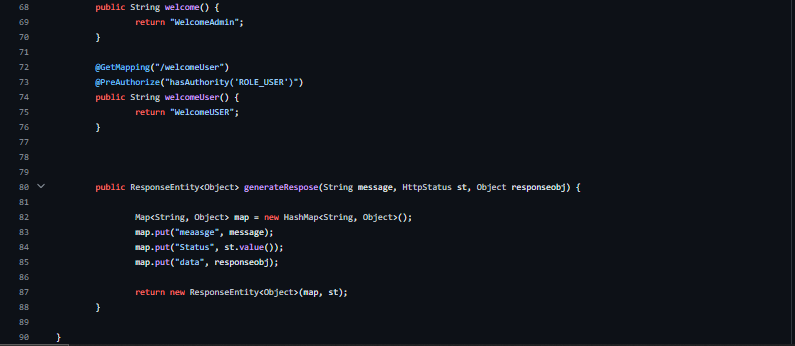
welcomeAdmin(), welcomeUser(): Endpoints accessible based on specific roles using @PreAuthorize.
Utility Methods:
generateResponse(String message, HttpStatus st, Object responseObject): Generates a response structure with message, status, and data.
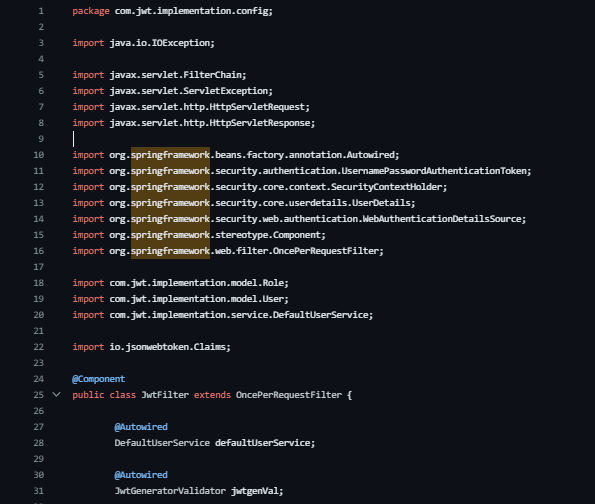
JwtFilter in Spring: Intercepting and Validating JWT Tokens for Authentication
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: The class is located in the com.jwt.implementation.config package.
Class Definition (public class JwtFilter): Represents a filter that intercepts and processes incoming requests.
Annotations (@Component, @Autowired):
@Component: Marks the class as a Spring-managed component.
@Autowired: Injects instances of required classes (e.g., DefaultUserService, JwtGeneratorValidator).
Methods:
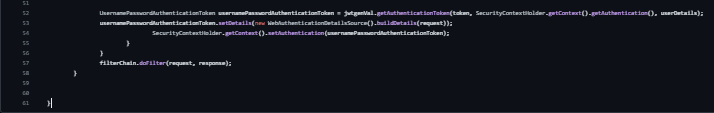
doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain): Overrides the doFilterInternal method from OncePerRequestFilter. It extracts the JWT token from the request, validates it, and sets the authentication in the security context.
JwtGeneratorValidator in Spring: Generating and Validating JWT Tokens for Authentication
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
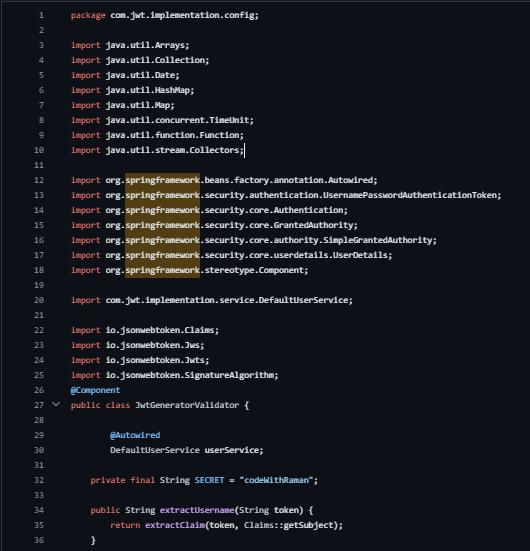
Package Declaration: The class resides in the com.jwt.implementation.config package.
Class Definition (public class JwtGeneratorValidator): Represents a class responsible for generating and validating JWT tokens.
Annotations (@Component, @Autowired):
@Component: Marks the class as a Spring-managed component.
@Autowired: Injects instances of required classes (e.g., DefaultUserService).
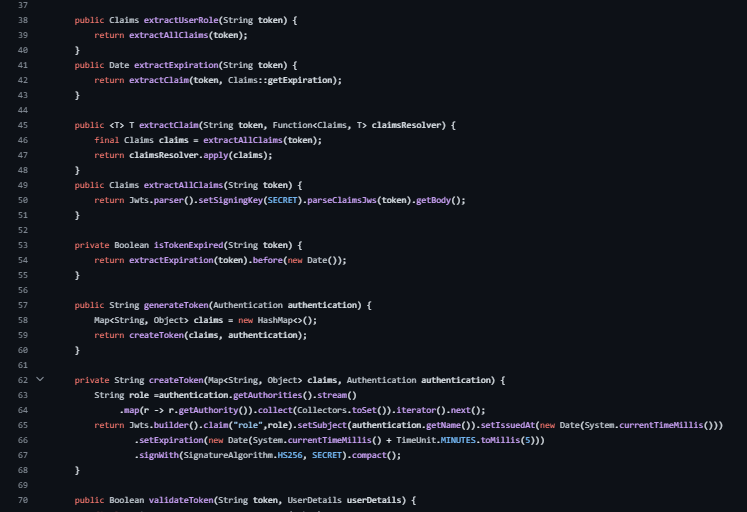
Methods:
extractUsername, extractUserRole, extractExpiration, extractClaim, extractAllClaims: Extract information from the JWT token.
isTokenExpired: Checks if the token is expired.
generateToken: Generates a JWT token based on authentication details.
validateToken: Validates the token against provided user details.
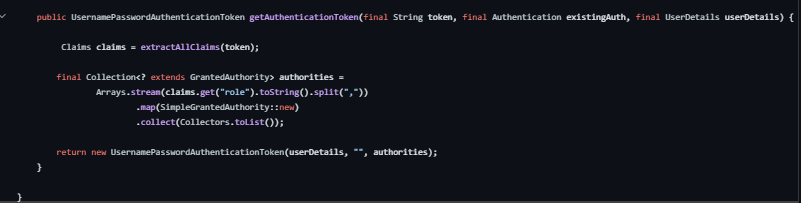
getAuthenticationToken: Retrieves the authentication token from the validated JWT token.
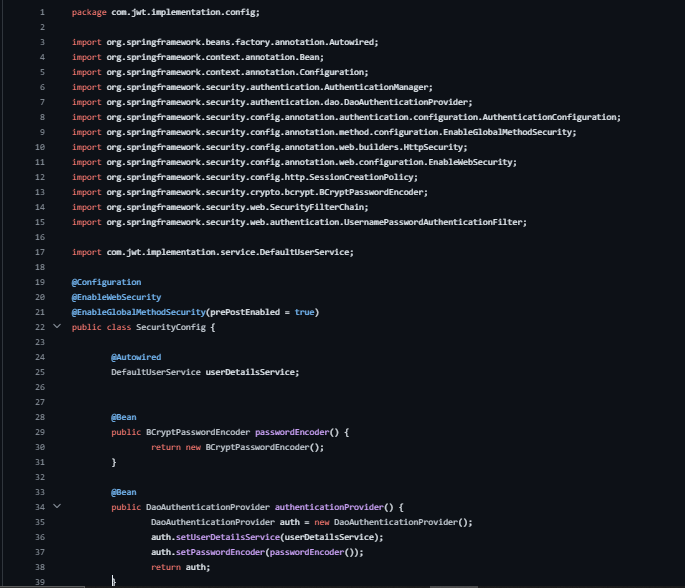
SecurityConfig in Spring: Configuring Web Security with JWT Authentication
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Code Explanation:
Package Declaration: The class is part of the com.jwt.implementation.config package.
Class Definition (public class SecurityConfig): Represents the configuration class for Spring Security.
Annotations (@Configuration, @EnableWebSecurity, @EnableGlobalMethodSecurity):
@Configuration: Marks the class as a configuration class.
@EnableWebSecurity: Enables Spring Security's web security support.
@EnableGlobalMethodSecurity(prePostEnabled = true): Enables method-level security.
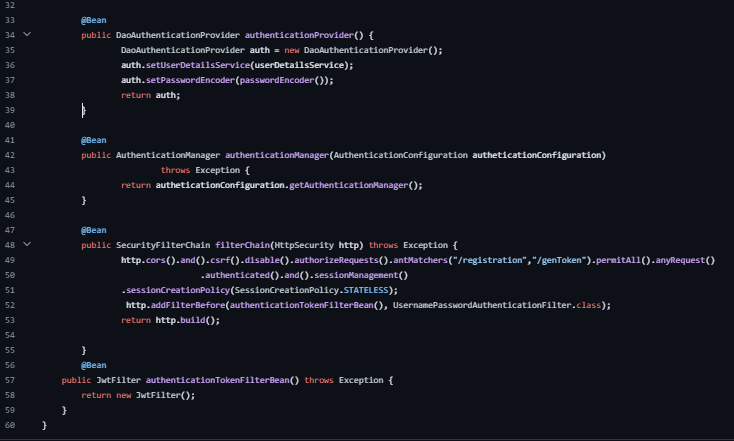
Beans and Configuration:
passwordEncoder(): Configures the password encoder.
authenticationProvider(): Configures the authentication provider.
authenticationManager(): Configures the authentication manager.
filterChain(): Defines security configurations for different endpoints and adds a JWT filter before the authentication filter.
Flow of the entire project:
The role-based user authentication project follows a structured flow orchestrated by various components and configurations within the Spring application.
1. Project Structure and Setup:
The project architecture comprises distinct packages, each responsible for specific functionalities. Configuration packages hold essential settings for security, database connectivity, and token handling. The model package defines entities like User and Role, which are persistently stored in the database. Repository interfaces manage database operations, while service classes handle user-related logic.
2. Database and Entity Setup:
The project relies on a PostgreSQL or MySQL database. The entity model includes User and Role, establishing relationships between users and their roles. Repository interfaces leverage JPA (Java Persistence API) to interact with the database, facilitating the storage and retrieval of user and role information.
3. User Registration and Authentication:
The REST API provides endpoints for user registration and authentication. Users register via the /registration endpoint, supplying details such as username, password, email, and role. The provided information is securely stored in the database after password encoding. Upon login attempts at /genToken, user credentials are authenticated. Successful authentication generates a JWT (JSON Web Token) containing user details and roles. This token is issued to the client for future authorization.
4. Role-Based Authorization:
Incoming requests are intercepted by a JWT filter (JwtFilter) before reaching secured endpoints. The filter validates the attached JWT token. Authorization checks are implemented using @PreAuthorize annotations on specific endpoints like /welcomeAdmin and /welcomeUser. These annotations verify the presence of required roles within the JWT token. Access to the endpoints is granted or denied based on the user's role extracted from the token.
5. Security Configurations:
The SecurityConfig class orchestrates the project's security settings. It defines rules for CORS, CSRF protection, and session management. The configuration also establishes authorization protocols by specifying access rules for different endpoints. The JWT filter is integrated into the filter chain to enforce token-based security.
6. Token Handling:
The JwtGeneratorValidator component manages JWT token operations. It orchestrates token creation, validation, and extraction. Upon successful authentication, this component generates JWT tokens, including user details and roles. Additionally, it validates incoming tokens attached to requests before granting access to secured endpoints.
FRONT-END:
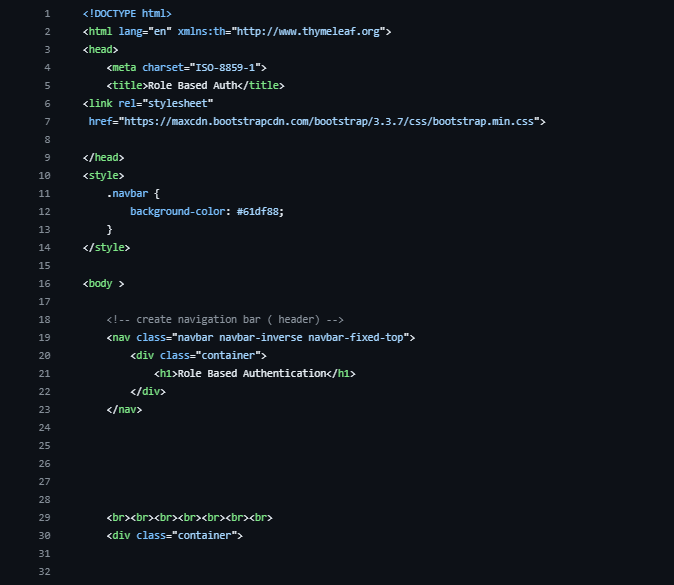
Dashboard.html:Main landing page
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
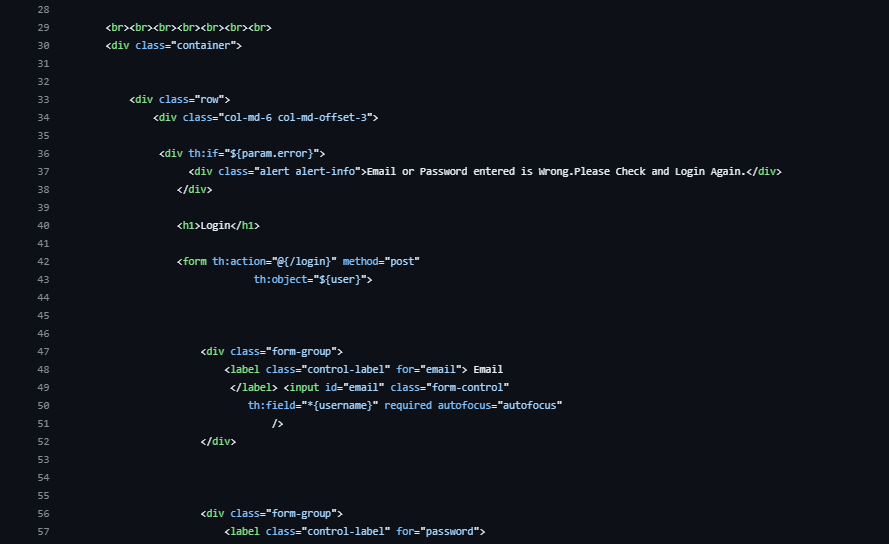
Login.html
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
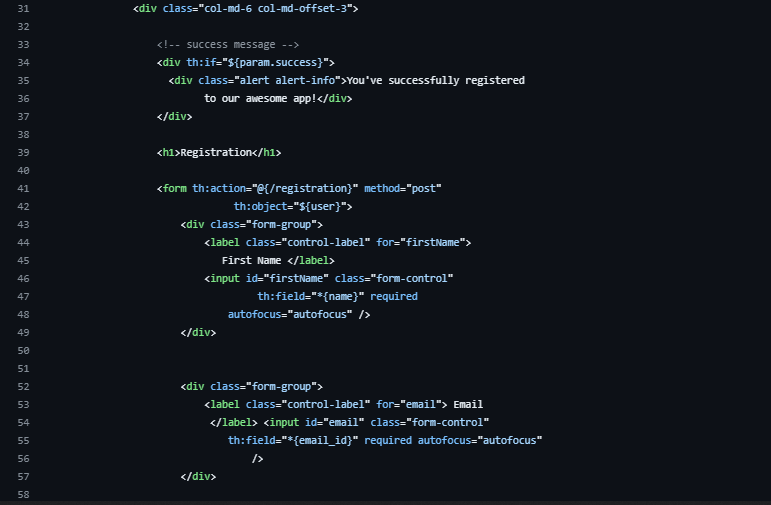
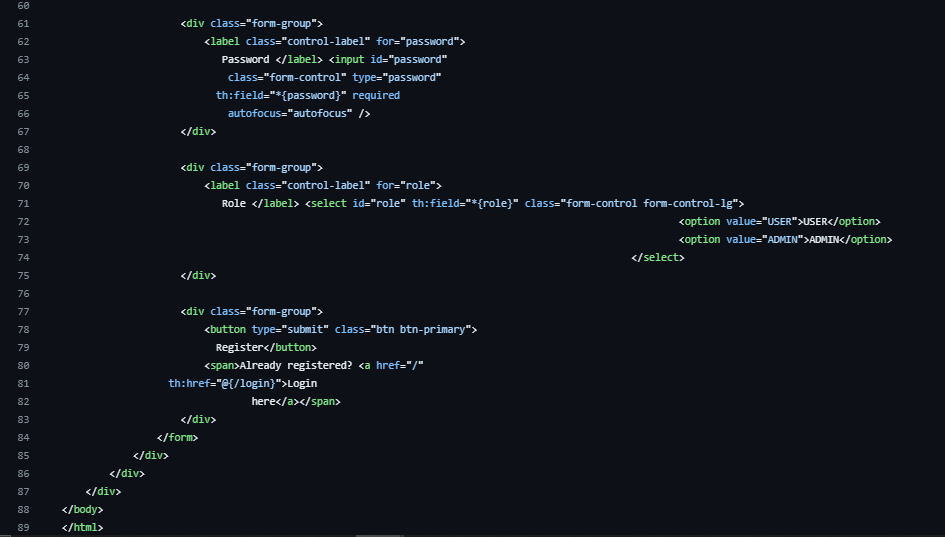
Register.html
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Conclusion:
In conclusion, this role-based user authentication project showcases a robust foundation for secure user registration, authentication, and role-based authorization within a Spring application. Leveraging technologies like JWT tokens, Spring Security, and database interactions, the project establishes a structured flow ensuring controlled access based on user roles. While the project comprehensively covers user registration, authentication, and authorization mechanisms, the creation of specific admin and user pages is intentionally left open-ended. This decision stems from the varied needs of different applications and user interfaces. Users can tailor the admin and user pages according to their unique requirements and preferences, integrating the provided authentication system seamlessly within their frontend interfaces